Meraki MX Firewall as a Cisco ISR Router
If you are looking for a solution so replace your aging fleet of Cisco ISR 2900 and 3900 routers – then you are not alone. See how we ended up with Meraki MX firewalls as this story unfolds.
Cisco’s end-of-life announcements ends software maintenance and security support at the end of 2020. By 2022 the entire lines are considered obsolete and no support is offered.
A metropolitan housing authority in Ohio has found themselves in this position. They have a couple dozen properties in the county with small connected management offices. They reached out to us for a solution.
The proposed solution is Meraki MX67W at each management office or branch.
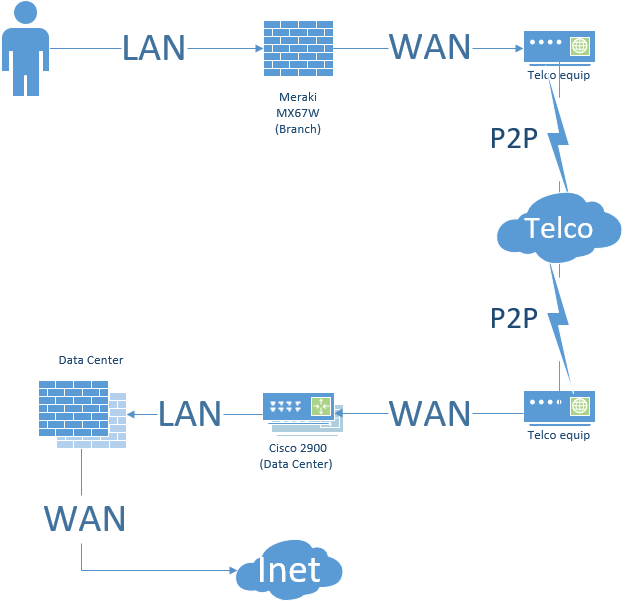
The unique component to this solution is their WAN topology. In this case, each branch is connected to a datacenter by a private MPLS cloud. Each branch then traverses a datacenter uplink for public access.
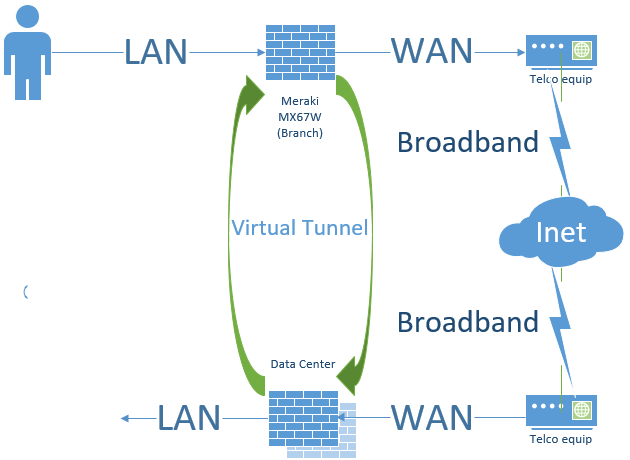
In contrast; most topologies will have direct internet access (DIA) to each branch, which is also used as IPSec VPNs for connecting to other sites.
The fundamental difference with the customer’s WAN topology is that there is no reason to firewall the branches’ uplinks to the datacenter. Further the datacenter can NOT be firewalled when reaching the branch. Similarly NAT (network address translation) breaks the organization’s access to each respective site.
Finally the point-to-point links, or the private MPLS, costs per megabyte are magnitudes higher than the cost per megabyte for broadband.
Our solution replaces the routers with firewalls but circumvents the firewall features for the inter-site traffic. Further, the design allows the customer a future transition to the far less expensive broadband without the purchase of any equipment.
The problem with the design is that Meraki MXs are managed thru the Meraki cloud, they call it their “Dashboard“. The MX will only connect with the Dashboard over a WAN interface that is both firewalled and NAT’d. But we cant have the uplink traffic inspected nor manipulated.
In our solution we proposed two options:
- “NAT Exemption” & firewall whitelist
- A dedicated link for Dashboard access
The problem with the NAT Exemption feature is that it is not fully supported by the vendor, Meraki. It has been in BETA testing for over two years.
The problem with the dedicated link for Dashboard access is that the Telco equipment may not have the extra port. Or the Telco may not provision more than a single port for the customer.
It remains to be seen which way this cookie crumbles when the customer weighs in. While both options have their associated risks, the design process and considerations were a good exercise.
Which way would you go if you were responsible for the environment after the IT consultant walked away?


